 Health care organizations are increasingly challenged to protect their networks and systems against cyberattacks and consequent data breaches.
Health care organizations are increasingly challenged to protect their networks and systems against cyberattacks and consequent data breaches.
In 2016, more than 1,000 data breaches were reported in the United States, a 40 percent increase compared with the previous year. Of the breaches, 377 were related to health care, a 63 percent increase, according to the Identity Theft Resource Center.
These breaches are often a result of missing technical controls and lacking user education and awareness. The HITRUST Common Security Framework (CSF)—a comprehensive and certifiable security framework used to protect sensitive information—provides a robust set of controls that health care organizations can implement to comply with Health Insurance Portability and Accountability Act of 1996 (HIPAA) requirements and help discourage further attacks. Beyond implementation of this framework, best practices exist to help organizations maintain compliance and continually improve cybersecurity.
A Valuable Target
Cyberattacks are increasingly complex, but many criminals still rely on decades-old techniques such as hacking and phishing, which is the practice of sending fraudulent emails appearing to be from reputable companies to solicit personal information. In 2016, these two techniques along with payment-card skimming accounted for 55.5 percent of all reported security breaches, according to the Identity Theft Resource Center.
Incidents with ransomware, which is malware that encrypts files and holds them ransom until a fee is paid, also increased in 2016. Ransomware infections are likely to continue to increase in 2017 as new versions are created and new distribution methods are designed. For example, a recent version of ransomware called WannaCry infected machines worldwide as it took advantage of unpatched Windows systems to spread laterally across networks, infecting multiple workstations and servers and causing significant service disruptions.
Hacking, phishing, and ransomware are so prevalent for health care organizations because medical records are worth 10 times more than credit card numbers on the black market, according to Reuters, making them a valuable target for hackers. They give thieves the information to:
- Create fake IDs
- Obtain pharmaceutical drugs for resale
- Commit insurance claim fraud
- Commit tax fraud
The value of this data means health care organizations are increasingly targeted, making it important to have the correct cybersecurity measures in place to protect patient, staff, and organizational data.
How HIPAA and HITRUST Work Together
It’s imperative that organizations take a proactive approach to securing their systems. The HITRUST CSF helps health care organizations advance their regulatory compliance and risk management practices by ensuring security and privacy controls are in place. It contains 149 control specifications divided into 14 control categories.
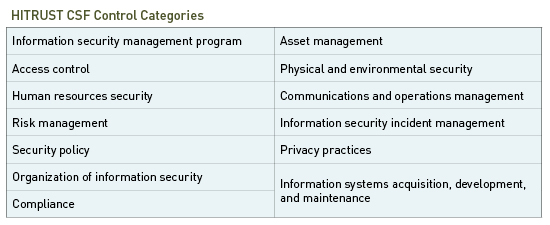
At a minimum, organizations must meet 66 control specifications to gain HITRUST certification, fulfilling the HIPAA Security Rule. The HITRUST CSF goes beyond the HIPAA Security Rule, however, by:
- Incorporating a number of additional regulations and compliance frameworks, such as PCI DSS, NIST CSF, COBIT 5, and ISO/IEC 27002:2013
- Providing prescriptive controls that are easy to understand
- Being certifiable
- Annually updating based on new security standards and regulations
Taken together, these elements can bolster a health care organization’s compliance and risk management practices by providing a single, unified approach to compliance and security.
Implementing Best Practices
Employing a framework like the HITRUST CSF isn’t enough to ward off continued cyberattacks. An organization that wants to fully protect its organizational and patient data must strive for continuous improvement through these five steps:
- Identify threats and vulnerabilities
- Protect sensitive information
- Detect malicious activity
- Respond to incidents
- Recover from attacks
Identify
The first step is to identify an IT network’s threats and vulnerabilities. A risk assessment can help determine:
- Assets that need to be protected
- Data that’s collected
- Location where data is stored and how it moves through the network
- People—including service providers and business associates—who have access to sensitive data
Protect
Once a company has identified its vulnerabilities, there are steps to protect its data and network through logical and physical access controls. These can include security awareness training administered to employees annually and during new-hire orientation as well as technical and administrative controls, such as:
- Encryption of data at rest and in transit
- Data life cycle management
- Data leakage protection
- Backup and recovery
- Network and application change management controls
- Software development life cycle
- Incident management and response
Detect
A company can then implement detection mechanisms to identify malicious activity. These mechanisms include:
- User access reviews that detect segregation of duties issues
- Anti-malware systems that detect and defend against malicious software
- A vulnerability management program that regularly identifies vulnerabilities and patches systems accordingly
- Security information and event management systems that can identify and correlate alerts generated by hardware and software
Respond
An organization must then be able to respond to an attack or incident. Having an incident response plan in place and personnel who’ve been trained on their roles and responsibilities is key. The response plan should be reviewed and updated annually with analysis performed to make sure there are adequate response times and support the necessary recovery activities.
Recover
An organization will need to recover after an attack, regardless of whether it’s been counteracted successfully. Business continuity and disaster recovery plans can help organizations efficiently restore operations. It’s best practice to adjust and test these strategies annually and when new operations are introduced to an IT environment.
Next Steps
A HITRUST CSF security assessment can help ensure a health care organization’s cybersecurity controls fulfill the HIPAA Security Rule and other compliance and regulatory requirements by identifying gaps and risks so that a company can build out corrective action plans.
Beyond the security assessment, there are a variety of additional assessment options available to health care organizations that allow organizations to report on their implemented controls, which can lead to HITRUST CSF certification.
We’re Here to Help
To learn more about how a HITRUST CSF assessment can help protect your organization from cyberthreats, contact your Moss Adams professional.